SPF 1.0 vs SPF 2.0 setup guide
Check your domain for DMARC, DKIM, SPF and MX records. Get a free report.
- The impact of Business Email Compromise
- A quiet Google update just made SPF more forgiving
- Cyber Insurance and DMARC Enforcement
- Email impersonation scams explained
- TLS-RPT Record
- SMTP Smuggling
- 🇩🇪 Welche Hosting Anbieter unterstützen DMARC
- Manual DMARC Monitoring vs Automated Monitoring
- Reverse Engineering Phishing
- DMARC Enforcement in 2026
- DMARC for non sending domains
July 22, 2024
Email authentication is important for securing your domain and ensuring your messages reach the inbox rather than the spam folder.
With a significant increase in email-based attacks like spoofing and phishing, technologies like SPF, DKIM, and DMARC have become foundational.
Among these, the Sender Policy Framework (SPF) plays the most major role. It helps in verifying the legitimacy of an email's source.
However, when there's research on SPF, confusion often arises between SPF 1.0 (the original protocol) and SPF 2.0 (also known as Sender ID).
What Is SPF 1.0?
SPF 1.0 is a common email authentication protocol that is designed to prevent sender address theft. It helps you as a domain owner to specify which mail servers are authorized to send emails on their behalf.
How SPF 1.0 Works?
When a mail server receives an incoming message, it checks the sending domain's DNS for an SPF record. This record helps in listing permitted IP addresses and domains. If the sender is authorized, the email passes SPF checks.
Examples of an SPF record: v=spf1 include:_spf.example.com ~all.
Syntax Breakdown:
v=spf1: This gives the version of SPF that is used. In this case, SPF version 1, the standard and most widely supported version.
include:_spf.example.com: Specify the IPs that are authorized to send emails.
all~: ("soft fail" mechanism) Any server not listed in this SPF record (or included domains) should not be trusted.
Alternative options:
-all = hard fail (reject)
+all = allow all (NOT recommended)
?all = neutral (no policy)
Benefits of SPF 1.0
Easy to implement via DNS TXT record.
It has a major role in DMARC alignment.
Helps you ensure message integrity.
What Is SPF 2.0 (Sender ID)?
SPF 2.0 is commonly known as Sender ID. It is developed by Microsoft as an extension of SPF. It builds on SPF’s principles, it focuses on a different email component for validation.
What It Does: Instead of verifying the MAIL FROM, Sender ID validates the PRA (Purported Responsible Address), the address in the visible "From" or "Sender" header field of an email.
spf2.0/pra spf2.0/mfrom spf2.0/mfrom,pra spf2.0/pra
"PRA" = Purported Responsible Address This checks the “From” or “Sender” address seen by the user in their email client (i.e., the header field defined in RFC 2822). It is used primarily to prevent spoofing of the visible sender address.
It’s the most common form of SPF 2.0 used in Sender ID.
spf2.0/mfrom "mfrom" = MAIL FROM
This checks the envelope sender (also known as the Return-Path, used in the actual SMTP transaction). It is the same address SPF 1.0 validates. It is useful for bounce handling and delivery notifications.
spf2.0/mfrom,pra This is a combined policy. It instructs mail receivers to validate both:
The envelope sender (mfrom)
And the header sender (pra)
Offers a more comprehensive level of authentication, but:
It requires more careful configuration.
It can cause issues with mailing lists or forwarded emails if not aligned correctly.
Sender ID (SPF 2.0): Is It Dead?
Despite a lack of active adoption, Sender ID is not completely dead, but it’s close.
SPF 1.0 alone is sufficient for Microsoft properties like Hotmail/MSN.
Sender ID is still read by some legacy systems but no longer updated or promoted. Most ISPs have abandoned Sender ID in favor of SPF 1.0 + DMARC.
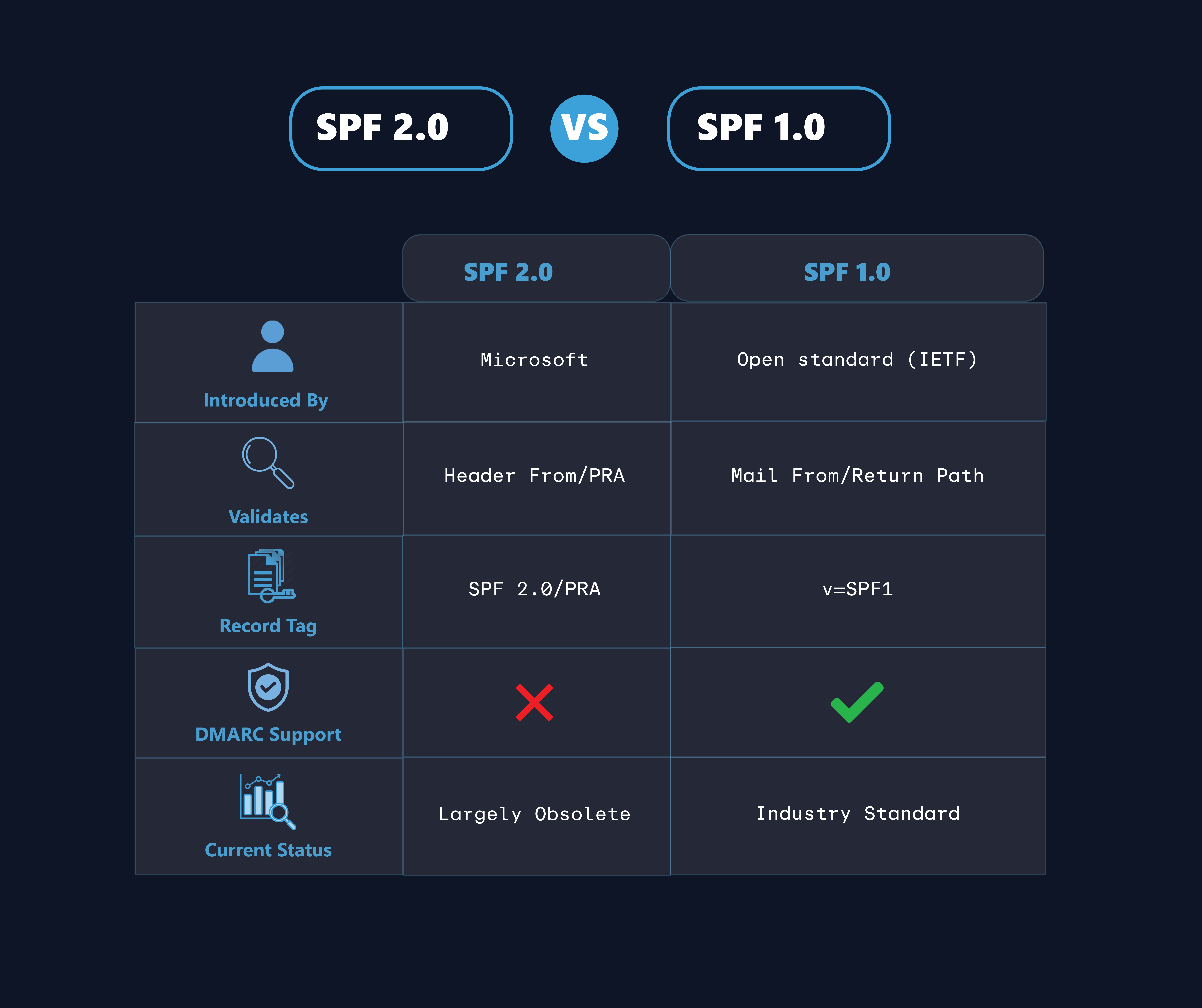
Major Differences Between SPF 1.0 and SPF 2.0
Sender Identity Validation SPF 1.0 is designed to authenticate the envelope sender (the MAIL FROM address used during the SMTP transaction). SPF 2.0 (Sender ID) includes validation to include the header "From" address; this enables a broader assessment of the sender’s identity by examining visible fields that end users see.
Policy Flexibility SPF 2.0 has greater flexibility and it allows domain owners to define authentication rules for multiple parts of the email. This specific approach helps to provide more nuanced control over sender verification.
Syntax Distinction SPF 1.0 records begin with the tag v=spf1. The SPF 2.0 (Sender ID) has the spf2.0/ prefix. It specifies its validation targets, such as spf2.0/pra or spf2.0/mfrom.
This distinction clearly signals to mail servers that the record is intended for use with the Sender ID framework.
Should You Publish Both SPF 1.0 and SPF 2.0 Records?
Publishing both records won’t be wrong. If you're sending emails to Hotmail/Outlook users, you may choose to add a Sender ID record for thoroughness.
Real-World Best Practices: Always publish a correct SPF 1.0 (v=spf1) record. Sender ID (spf2.0) is optional, primarily for edge-case Microsoft support. Most spam filters and authentication checks ignore spf2.0 records today.
SPF, Sender ID, and DMARC: What WorksTogether?
DMARC relies on SPF 1.0 and DKIM to authenticate email messages. Sender ID is not supported by DMARC and should not be relied on for compliance. Therefore, SPF 1.0 is essential for any organization implementing DMARC policies.
If you’re building a modern email authentication framework (SPF + DKIM + DMARC), you can safely ignore Sender ID.
Conclusion:
SPF 1.0 and SPF 2.0 (Sender ID) were both developed to authenticate email senders and combat spoofing, but they focus on different parts of the email structure.
SPF 1.0 is the current industry standard, widely supported, and compatible with modern protocols like DMARC, validating the MAIL FROM or Return-Path. SPF 2.0 (Sender ID), introduced by Microsoft, adds the ability to validate the visible "From" header, but it is now considered largely obsolete and lacks DMARC compatibility.
FAQs
Is SPF 2.0 still in use today? SPF 2.0 (Sender ID) is still supported by some legacy Microsoft systems (like Hotmail), but it's no longer considered a modern or widely adopted standard. Most major providers rely on SPF 1.0.
Should I publish both SPF 1.0 and SPF 2.0 records? It’s not required, but if you're concerned about delivery to Microsoft domains, publishing both won’t hurt. However, SPF 1.0 should be your priority.
What’s the difference between “mfrom” and “pra” in SPF 2.0? mfrom validates the envelope sender (like SPF 1.0), while pra checks the header sender (the visible "From" address).
Does SPF 2.0 improve DMARC compliance? No. DMARC only supports SPF 1.0 and DKIM. SPF 2.0 is not used in DMARC alignment or policy enforcement.
SolarWinds SPF, DKIM, and DMARC Records Configuration
DMARC, DKIM, and SPF are essential email security standards used by inbox providers like Google and Yahoo. These DNS records verify that your emails come from a legitimate source and are safe to open. Authenticating your domain ensures that your emails are not marked as spam. Solar Winds provides SPF, DKIM, and DMARC records for sender domain authentication. This article will guide you step-by-step through the domain authentication process. So, keep reading!
Read more →
Check domain and follow the instructions to nail down your DMARC configuration.
No expert knowledge needed!